Linux SSH 基于密钥交换的自动登录
先来说说 ssh 密钥登陆的流程
什么是 ssh?
SSH 全称 secure shell,是一种网络传输协议,是最常用的安全管理远程服务器的协议和工具集。
SSH 协议中使用多种加密技术保证在用户终端和服务器之间建立加密安全连接,连接双方通过互相握手验证,并通过加密的通道传递管理命令和执行结果。
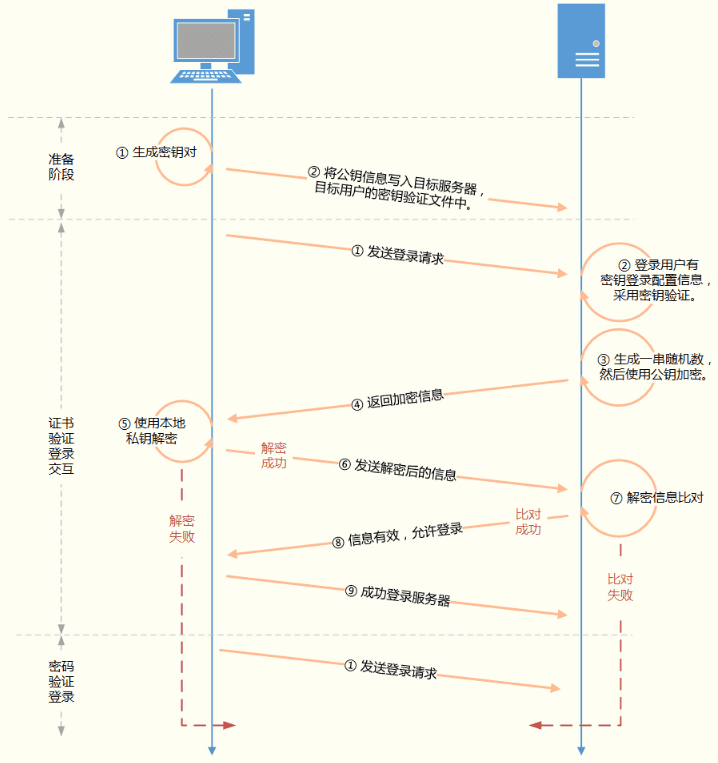
协商交互的过程
01客户端向目标服务器发送登录请求。在SSH服务启用了证书验证登录方式后,会优先通过证书验证方式进行登录验证。02目标服务器根据SSH服务配置,在用户对应目录及文件中读取到有效的公钥信息。03目标服务器生成一串随机数,然后使用相应的公钥对其加密。04目标服务器将加密后的密文发回客户端。05客户端使用默认目录或-i参数指定的私钥尝试解密。06如果解密失败,则会继续尝试密码验证等其它方式进行登录校验。如果解密成功,则将解密后的原文信息重新发送给目标服务器。意思类似于:“看,这是这段话的原文。我能读懂发过来的密文,我拥有服务器的控制权,请让我登录。”07目标服务器对客户端返回的信息进行比对。如果比对成功,则表示认证成功,客户端可以登录。如果对比失败,则表示认证失败,则会继续尝试密码验证等其它方式进行登录校验。
以下是流程图
再来说说怎么实现
通过例子来教你怎么实现 ssh 密钥交换登陆
先准备两台 linux 机器,配置好 IP 地址,用 xshell 连接好,如下图
在 0.4 机器上操作,创建密钥文件,此处不做其他配置
其中 id_rsa.pub 是公钥,id_rsa 是私钥
最后记得需要把 /root/.ssh/ 权限设置为 700
如需要其他配置,请看下面参考文档
http://www.jinbuguo.com/openssh/ssh-keygen.html
[root@software ~]# mkdir .ssh
[root@software ~]# cd .ssh/
[root@software .ssh]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:4cS89XlMHNSIpCM8HorHI8EXFwqrzQWk35x+0AI8q+8 root@software
The key's randomart image is:
+---[RSA 2048]----+
| .+ . o. ..ooo |
| + + B ......|
| . B + X + o |
| = % B B o + |
| . B @ S o o |
| . + + . |
| . . . |
| . . |
| .E |
+----[SHA256]-----+
[root@software .ssh]# ll
总用量 8
-rw-------. 1 root root 1679 4月 29 15:51 id_rsa
-rw-r--r--. 1 root root 395 4月 29 15:51 id_rsa.pub
[root@software .ssh]# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAyOXUPsdu2ZahtWKw5HYD+N9vrxEx+RtDQTCNwG+paYHkDhzh
y06jWU8MppNXPWMe/qFv4GEDBxxvvTdlXDSPCrxbv4Rdg9bMGcnsaVzq8b3Yg85S
ZJA3ZeqYwvIa5BwlTZPI8Oa2BD4UDEe8Ymwi0FkflbagfYYl57Moesy9O05Q97Hr
FqeXmvSd3ugVm756rHwt2/2nLaO6VlCXOmii0j54pl9uoCZ41xvcLG/nb5KL8+G5
GHnfsQLACjyTBZZbVthsgdOs7pf3pTqga/af7rg4AquwV2i9eN5JQ3IOPqd4V3Ai
z3scmhvMycJ40qZaskrEbc3StczGITJuHLipZQIDAQABAoIBAQC2IzCnbjaAzUF0
6rIHnzuAskpWRVeySlZSTwvlMRc+EcZKSUMpCPWt7a5Bg4nvnOMn5gNBQZL2KoDf
4s5hp0EccaMY4o/KDL7kjp5o9BYJ753R+gfXJq0jGGtBKzDYKPBlAhyG1BSnigSx
EYSpEvMJRBQPrxCYXTwWcea8Vs0lawNChryP33BryAbWyGPf1TsP8CJ3//A8e1vD
iYDocQ7vYW53iYK0R0I0rHnH2yK00SimqRTtuFbvDEs32home3Xyl6I3E4gJfjlH
6Nx1T+gY/rp8C2ghF/Bpi+0TkzI0CE8/YtcGUcP5gVxy1DeAnIi71d0SYYQRlX8Y
oRaV3Q0BAoGBAOidZFaG/JYtzm+o3XROl80HphQ17dILcj3a/K1ZMTfDMpgESHPU
z/GjlIPk6qyrYLrRbGwzdjFDBM7Z2Xh15NnJ86b25WeDf4Vh8tTxUbM5kY+2C5vI
Skiv9M/twwobBOmNd/FEuGKDFmIUDTdenVbflwKCtwqOuGMPFSuzkrklAoGBAN0Y
Ka1MVHerMty2NNedHwxf9ZS0PU3ELbgz53P5BFbEnFJW+ZTeR0lptbhMQYBXO4Ag
WjxnAp5f2Jg66nF99PMwCbjyIB7Rb1Zj7g0FC61SKLBg+H2ZUSTVZ8Ebvclptgbd
Xbsc3SVDcwR3sCuREOF9t9emRUX0/8fZ385QMdtBAoGBAKxW597/laYCe/7YQnKI
RAmAkDhLGE7VcieH1krsWP2yXgqoqbE/y2yAwGjTslaJhloDDOxBWGD5AVfrqSaJ
WitNZ3qdU6tUjqcYwZuoytoZXdH2kzUwuHCQBLYEtssG56XNzT5wppc9/dheeMg8
DiAt+ai/hbOJt+yUYSAGpD8NAoGBAMjPHWttHHrkX3nfc/cxmfWfYmoBmnx7Zhsb
6WiID8zPHjwbCuyPRqgC/y249PUgRcaFm++oj9RQsWTyfeU+xa/rPalhIJNdHYaV
lKz2nDh7msE4EfnhurV9rpLSI3pALTfm7y73dFRYAqtYGgY35+EmUkfnmJuFfpuB
46h7Zg0BAoGAJEbd2QWxqUS8aXFs7iDljoALLelb4RAj5OBdECLdeQTdyXx8mvJS
uMDXNZGwo2ixbxvo5CB6+DIzram+8sAZypAsyNdid/+AjNpDRntj2UCDI/2gEOVg
UXk03DBn3dg/LyRMVb7bnd8vmQlLkFap9YChCsPOSL4E/P6u89pkO5o=
-----END RSA PRIVATE KEY-----
[root@software .ssh]# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDI5dQ+x27ZlqG1YrDkdgP432+vETH5G0NBMI3Ab6lpgeQOHOHLTqNZTwymk1c9Yx7+oW/gYQMHHG+9N2VcNI8KvFu/hF2D1swZyexpXOrxvdiDzlJkkDdl6pjC8hrkHCVNk8jw5rYEPhQMR7xibCLQWR+VtqB9hiXnsyh6zL07TlD3sesWp5ea9J3e6BWbvnqsfC3b/acto7pWUJc6aKLSPnimX26gJnjXG9wsb+dvkovz4bkYed+xAsAKPJMFlltW2GyB06zul/elOqBr9p/uuDgCq7BXaL143klDcg4+p3hXcCLPexyaG8zJwnjSplqySsRtzdK1zMYhMm4cuKll root@software
[root@software .ssh]# chmod 700 /root/.ssh/
在 0.3 上操作
创建 .ssh 目录并授予 700 权限,创建 authorized_keys 文件并授予 600 权限
把 0.4 的公钥内容复制到 authorized_keys 并保存
[root@jenkins ~]# mkdir .ssh
[root@jenkins ~]# chmod 700 .ssh/
[root@jenkins ~]# cd .ssh/
[root@jenkins .ssh]# touch authorized_keys
[root@jenkins .ssh]# vim authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDI5dQ+x27ZlqG1YrDkdgP432+vETH5G0NBMI3Ab6lpgeQOHOHLTqNZTwymk1c9Yx7+oW/gYQMHHG+9N2VcNI8KvFu/hF2D1swZyexpXOrxvdiDzlJkkDdl6pjC8hrkHCVNk8jw5rYEPhQMR7xibCLQWR+VtqB9hiXnsyh6zL07TlD3sesWp5ea9J3e6BWbvnqsfC3b/acto7pWUJc6aKLSPnimX26gJnjXG9wsb+dvkovz4bkYed+xAsAKPJMFlltW2GyB06zul/elOqBr9p/uuDgCq7BXaL143klDcg4+p3hXcCLPexyaG8zJwnjSplqySsRtzdK1zMYhMm4cuKll root@software
[root@jenkins .ssh]# chmod 600 authorized_keys
在 0.4 上测试 ssh 免密登录到 0.3
测试登陆正常
[root@software .ssh]# ssh [email protected]
The authenticity of host '192.168.0.3 (192.168.0.3)' can't be established.
ECDSA key fingerprint is SHA256:EUBOnj/vYhRm+dEZxEW+eLg6Qyp8D0wDcBGZCRDc7J0.
ECDSA key fingerprint is MD5:60:51:92:07:30:7b:57:6c:c8:e1:9f:da:70:ea:f1:be.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.0.3' (ECDSA) to the list of known hosts.
Last login: Mon Apr 29 15:46:38 2019 from desktop-7gtlj78
[root@jenkins ~]# ifconfig
enp0s3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.3 netmask 255.255.255.0 broadcast 192.168.0.255
inet6 fe80::a00:27ff:fe6d:d1f4 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:6d:d1:f4 txqueuelen 1000 (Ethernet)
RX packets 2480 bytes 2389961 (2.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1686 bytes 139564 (136.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 32 bytes 2592 (2.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 32 bytes 2592 (2.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@jenkins ~]# exit
登出
Connection to 192.168.0.3 closed.
[root@software .ssh]#
至此,ssh 基于密钥交换的自动登录就完成了~
本文链接:
/archives/sshkey
版权声明:
本站所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自
Linux 小白鼠!
觉得文章不错,打赏一点吧,1分也是爱~
打赏
 微信
微信
 支付宝
支付宝
 微信
微信
 支付宝
支付宝